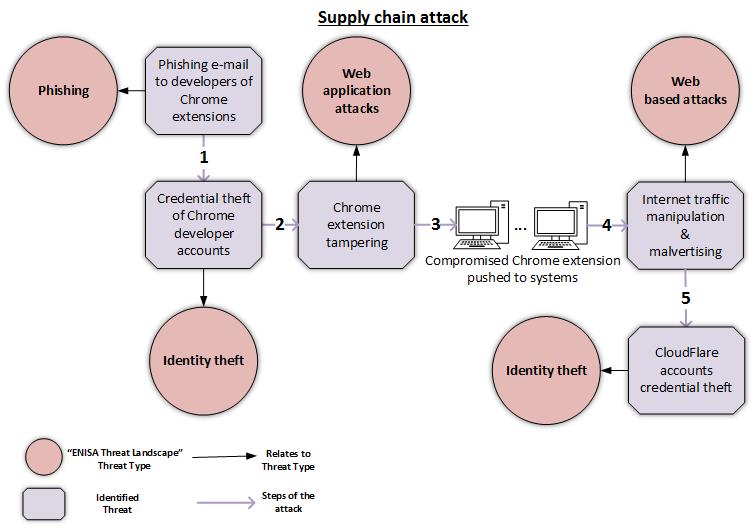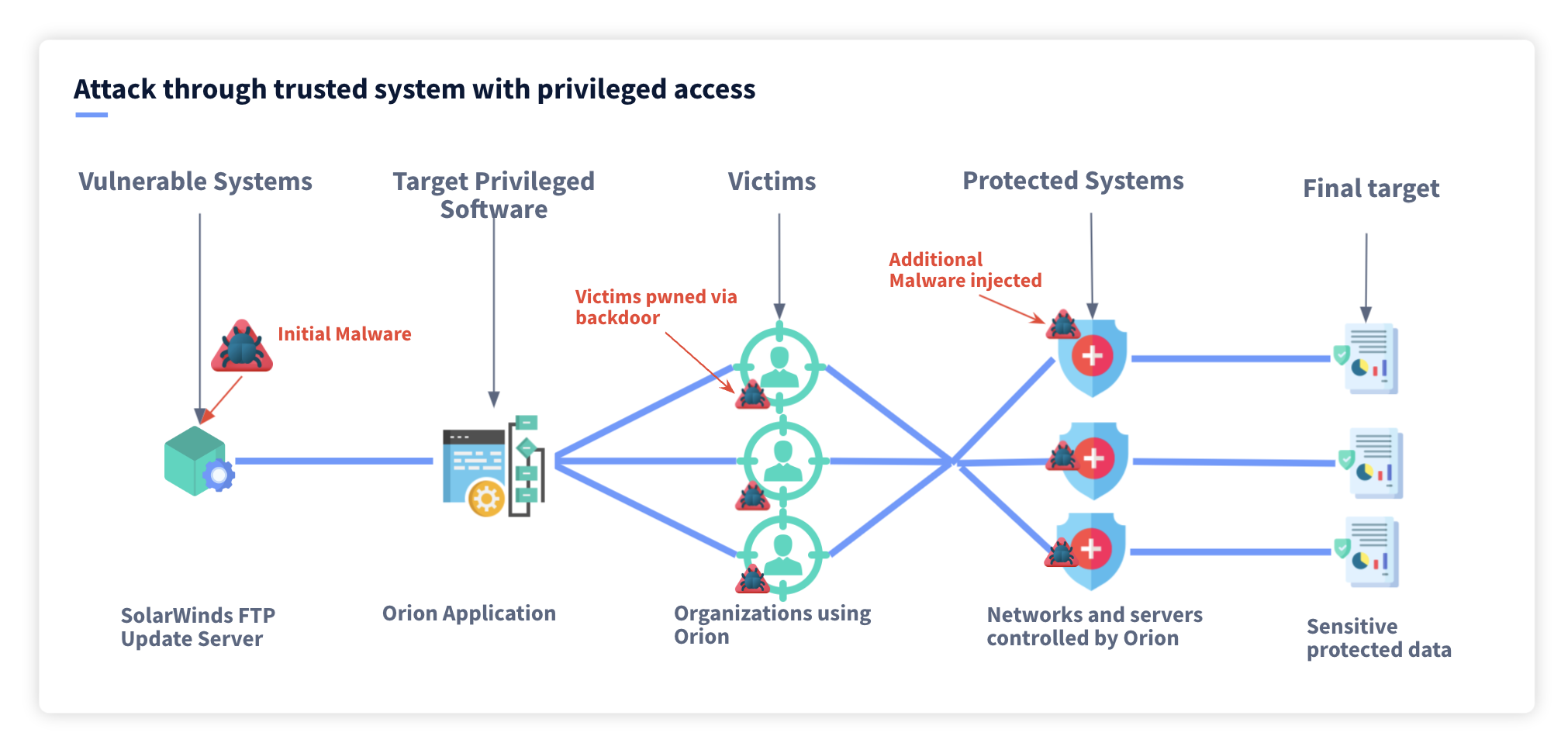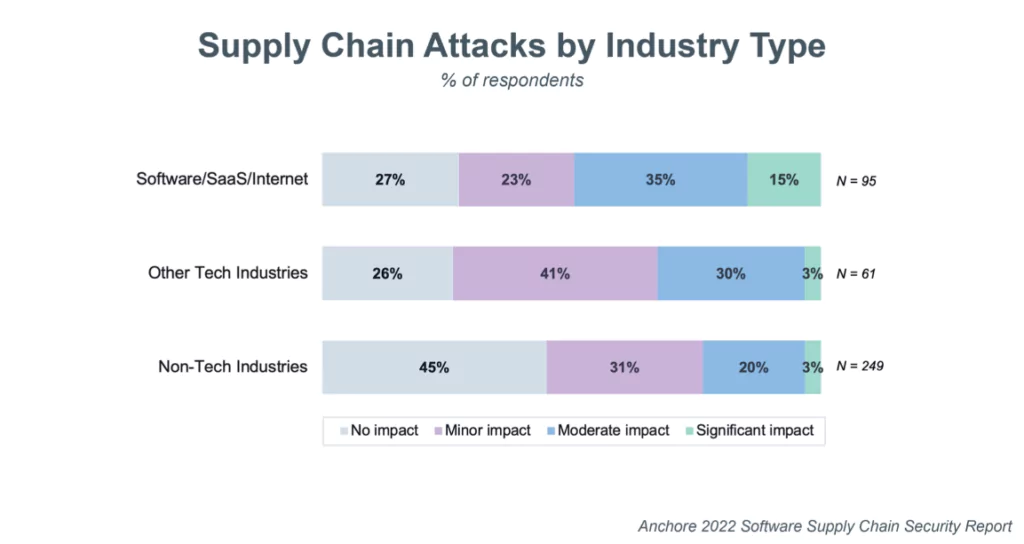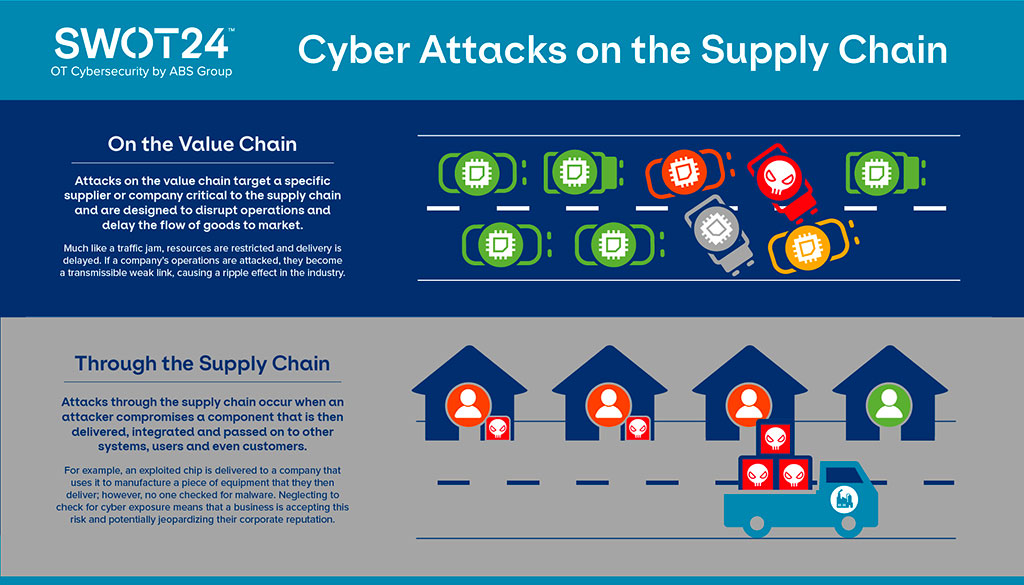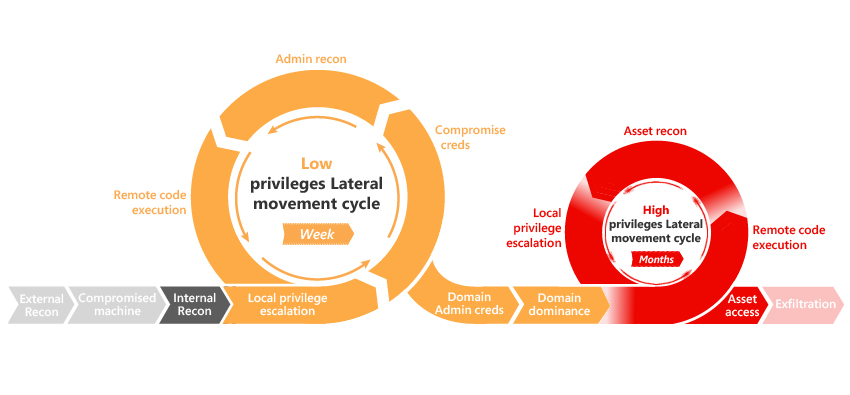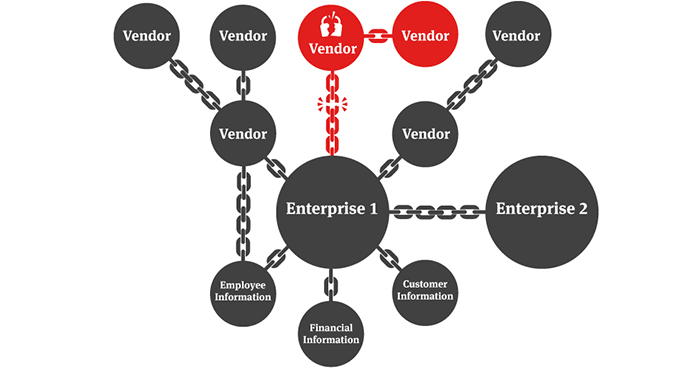
Six degrees of separation: cyber risk across global supply chains | United States | Global law firm | Norton Rose Fulbright
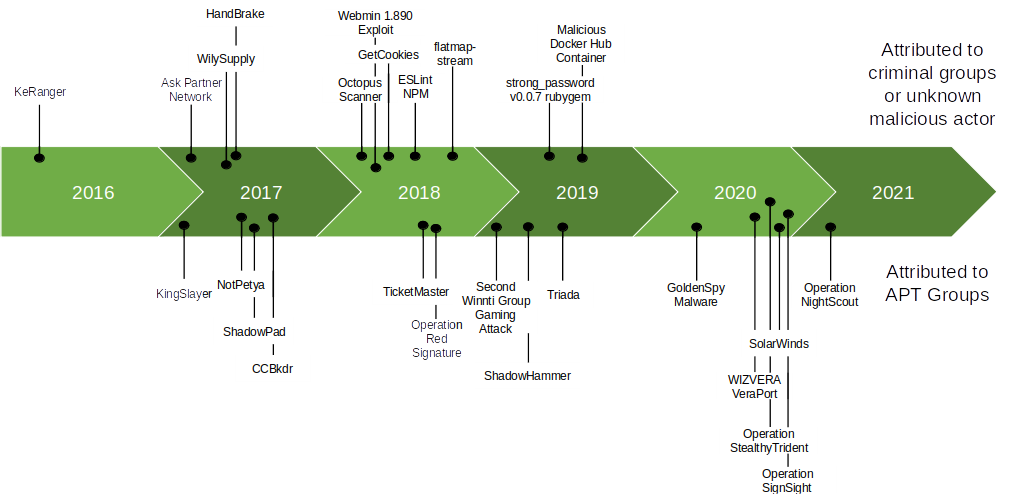
A Guide to Supply Chain Compromises: Don't let your supply chain be the chink in your cyber armour - Airbus Defence and Space Cyber