DER protocol level attack categories including data and/or command (a)... | Download Scientific Diagram

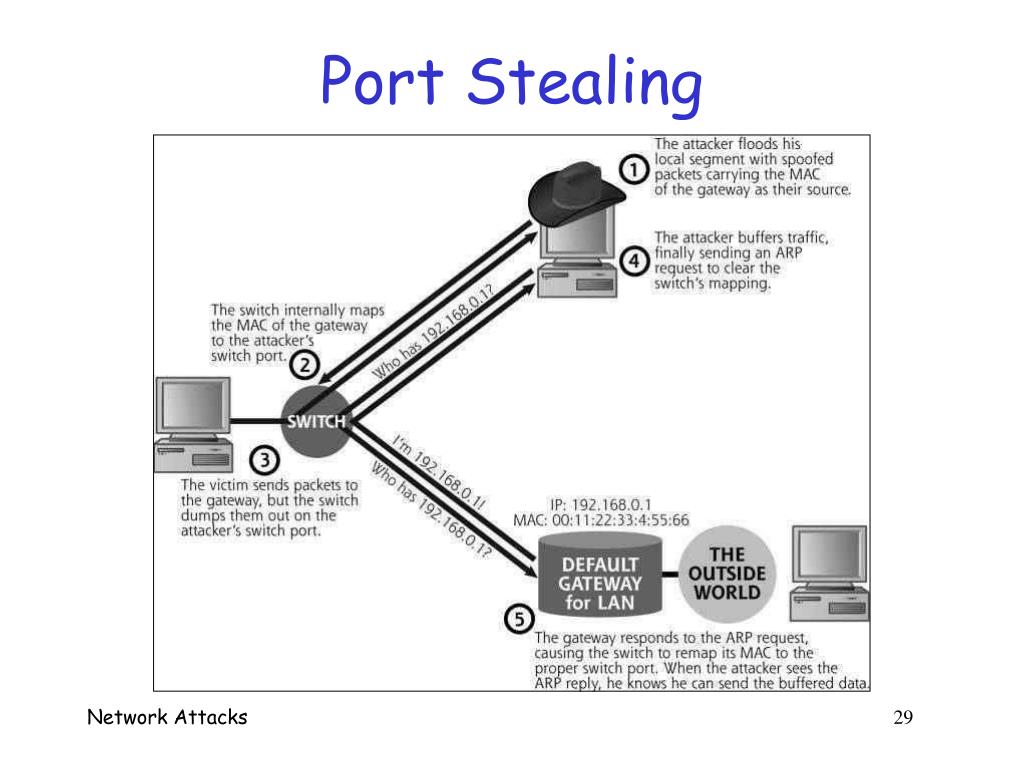
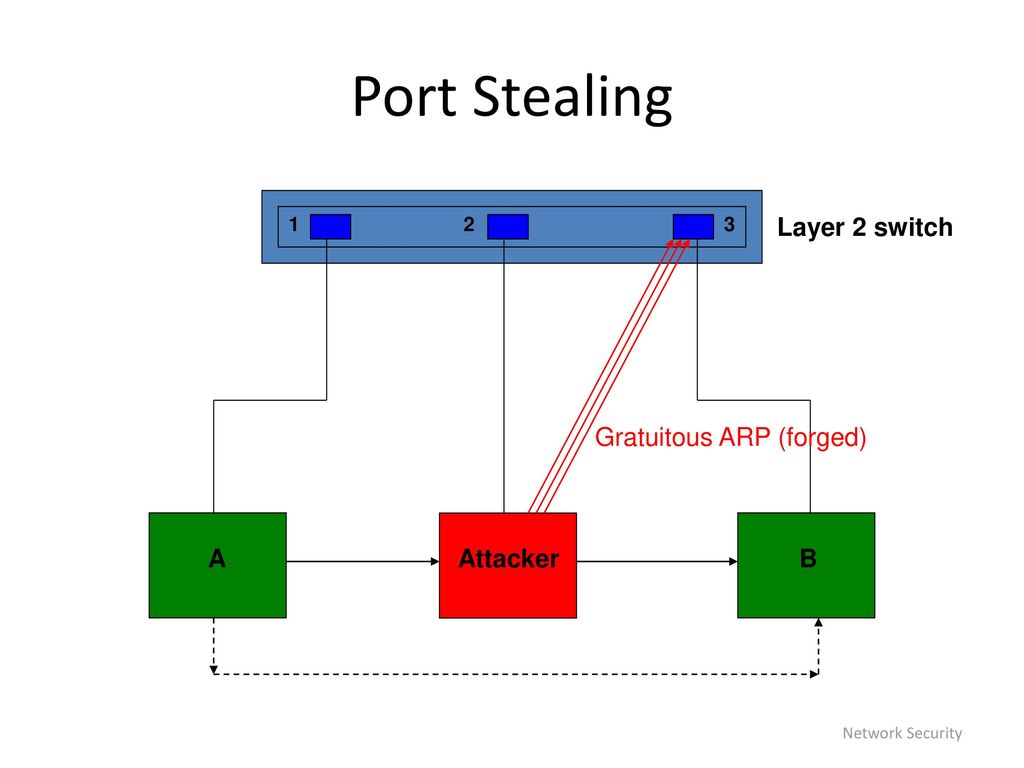
The attacker performs a port stealing attack targeting the PLC via the... | Download Scientific Diagram

Amazon.com: WiFi Extender,WiFi Extender Signal Booster for Home,Covers Up to 4000 Sq.ft and 32 Devices WiFi Range Extender,nternet Repeater, Long Range Amplifier with Ethernet Port,Access Point,Alexa Compatible : Electronics

Threats Behind Default Configurations of Network Devices: Wired Local Network Attacks and Their Countermeasures | SpringerLink












/cloudfront-us-east-1.images.arcpublishing.com/gray/3CRWZK574FCNNMOQVLEZXUOIGI.jpg)

