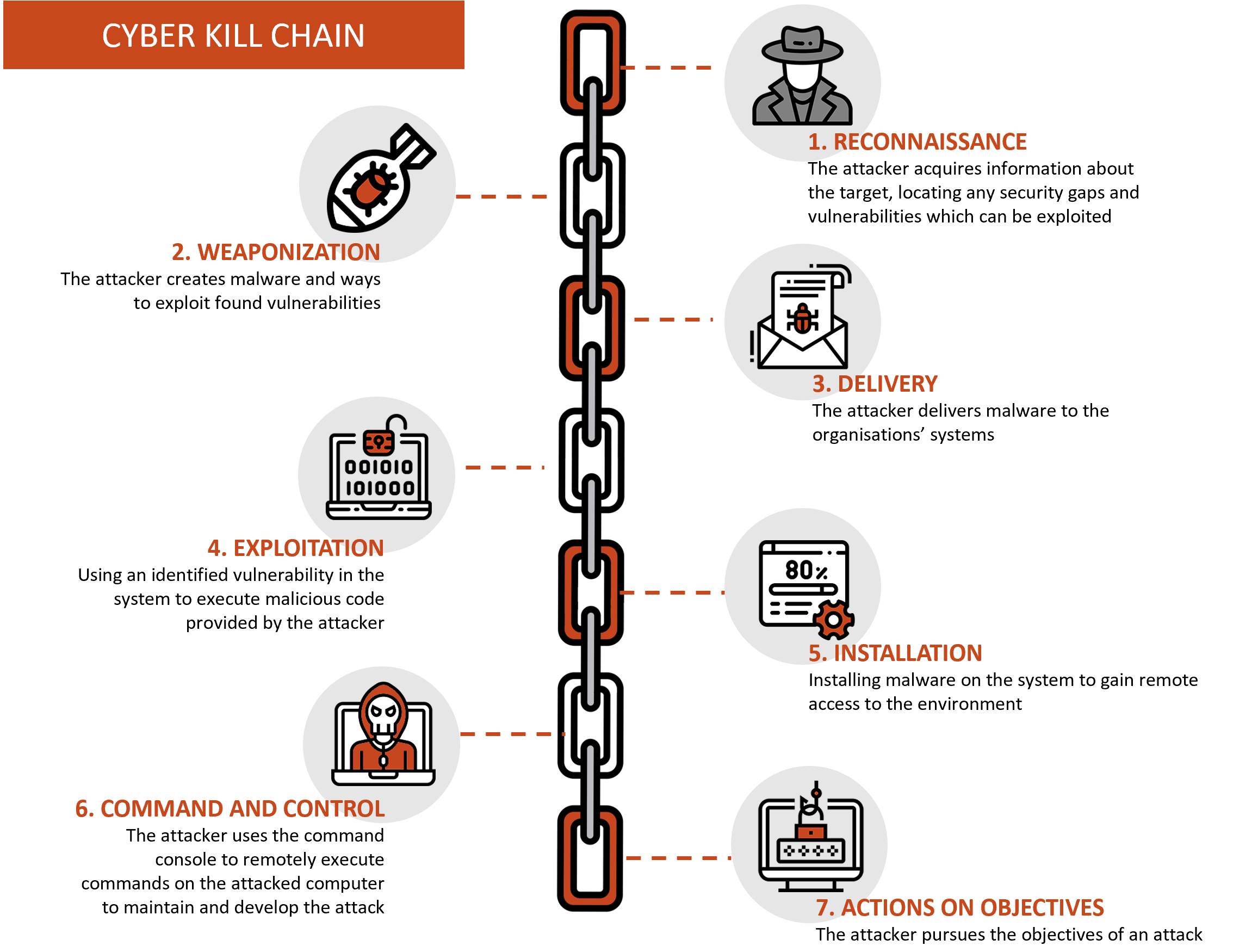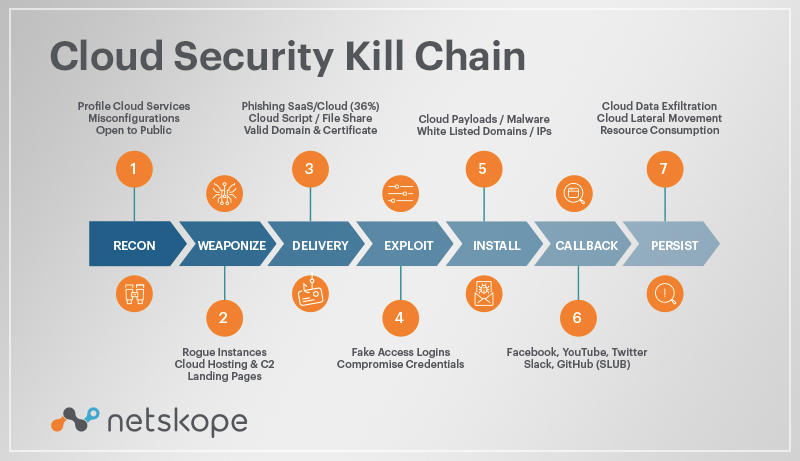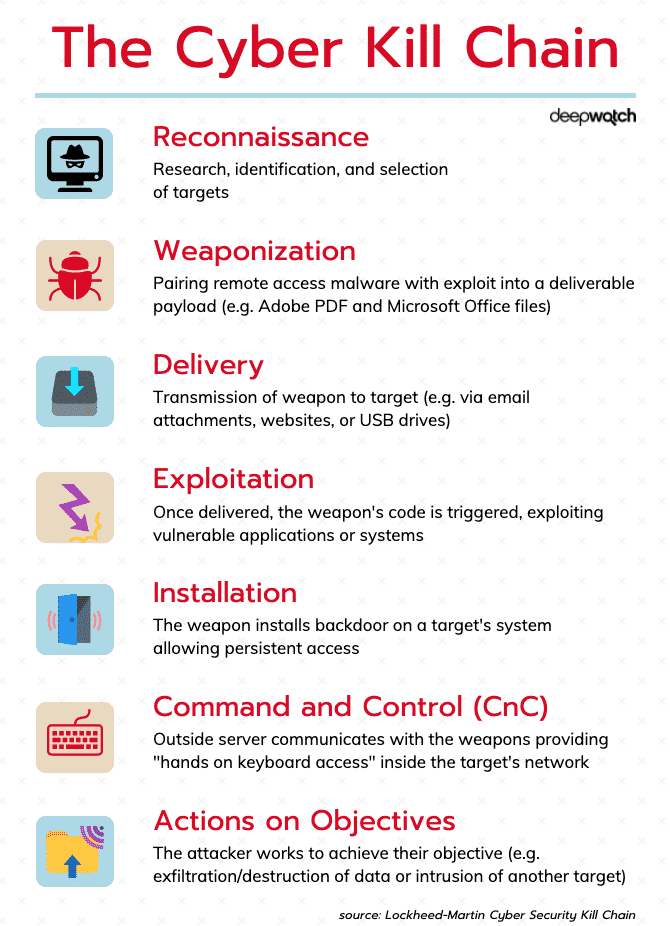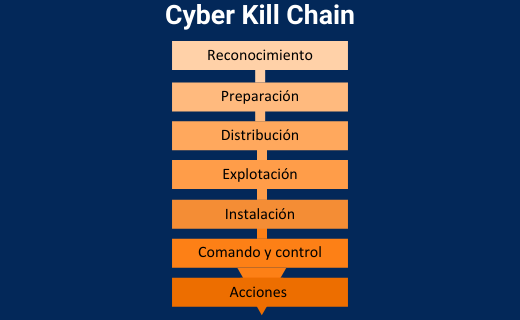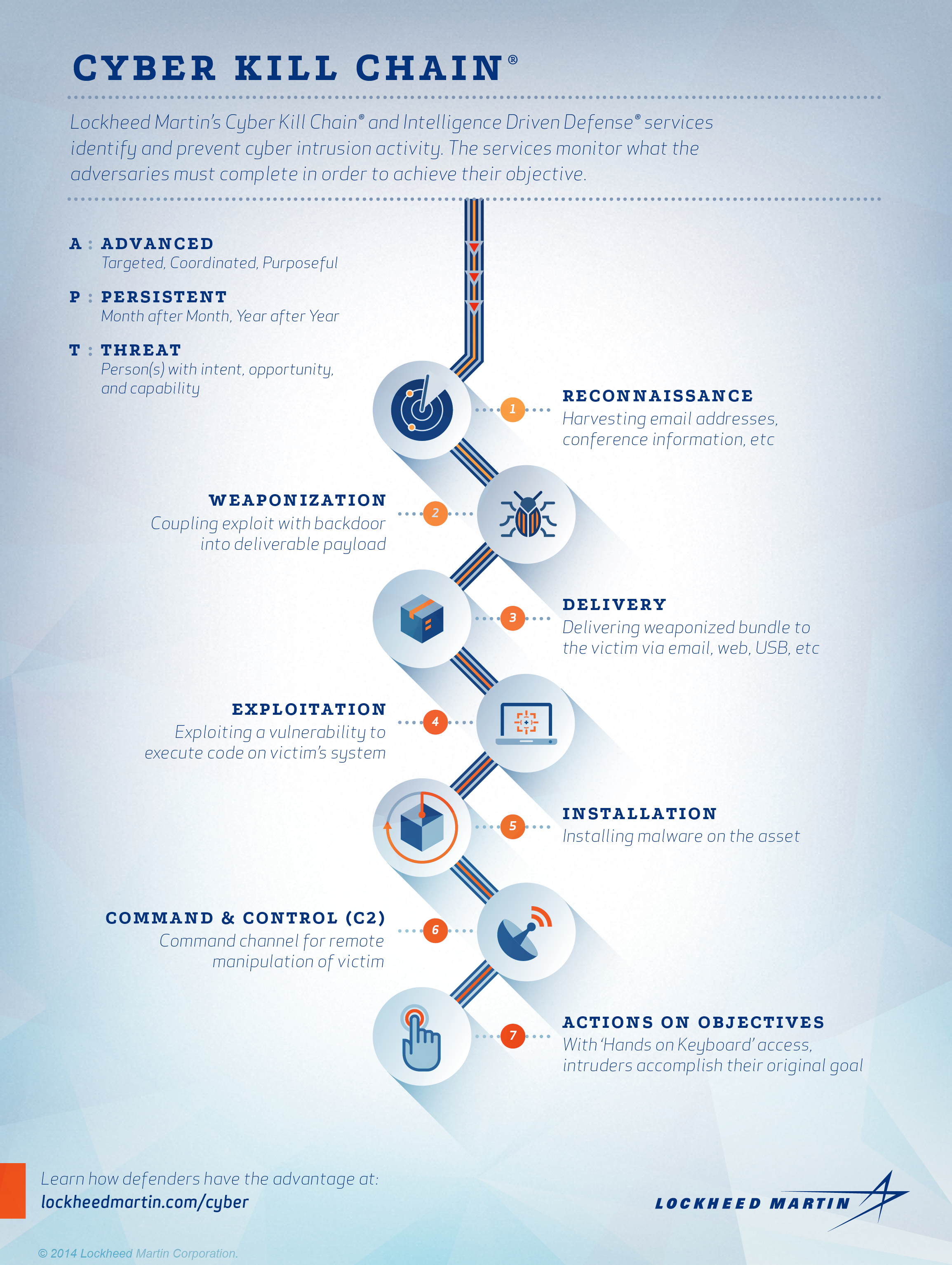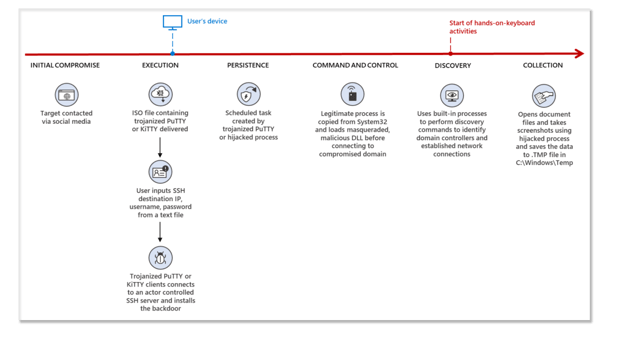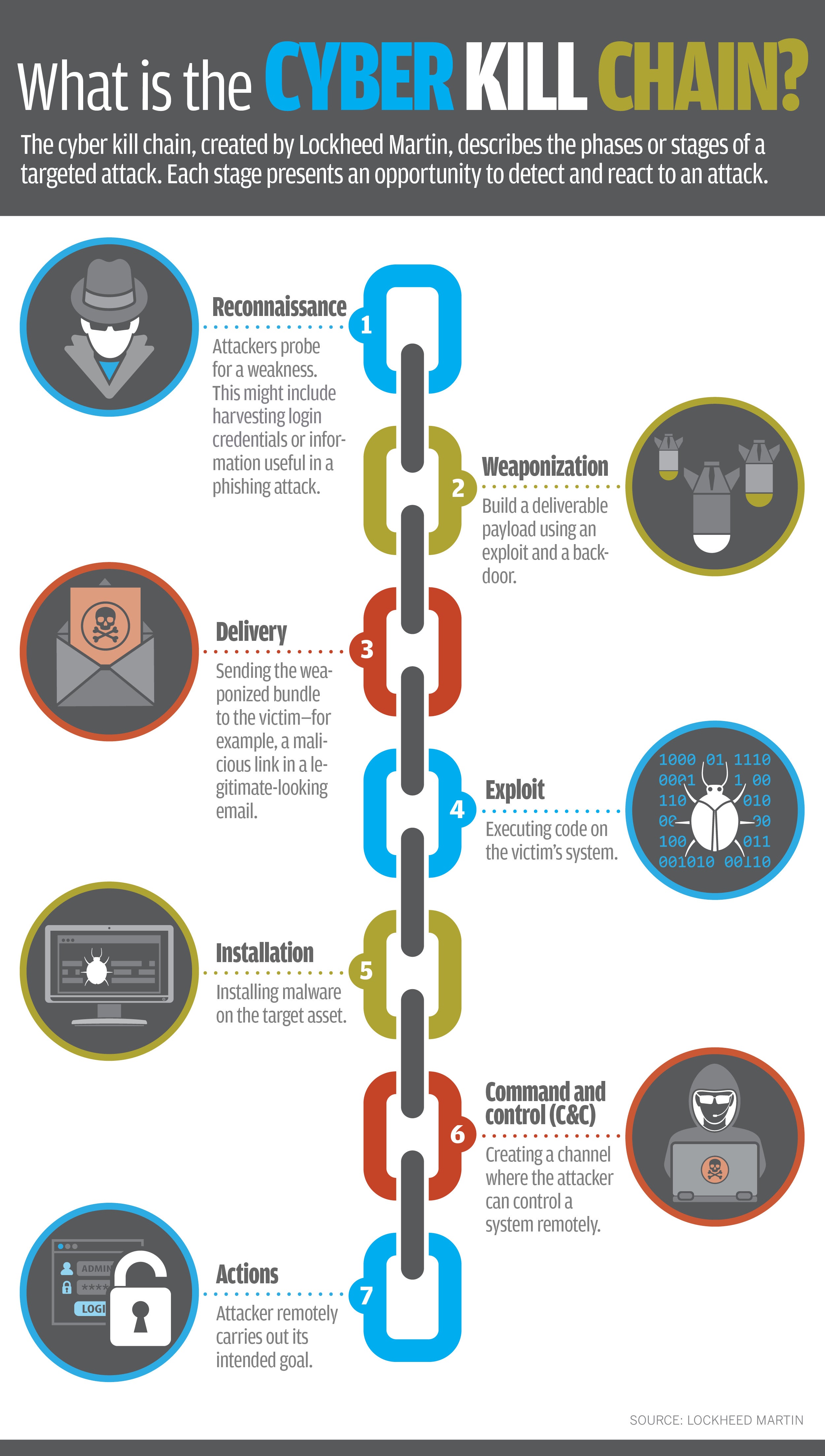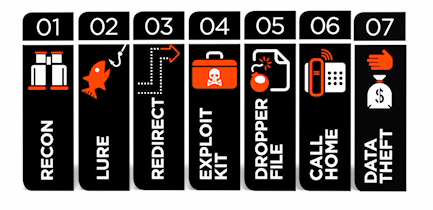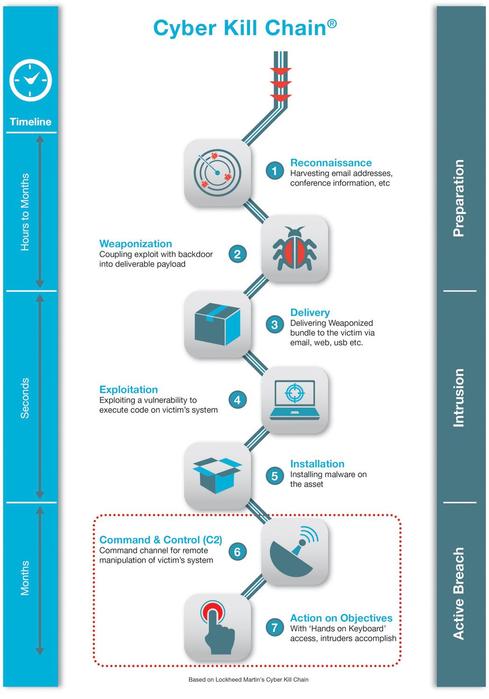
Is the Cyber Kill Chain Model the Ultimate Solution to Rising Ransomware Attacks? - United States Cybersecurity Magazine

Learning By Practicing - Hack & Detect: Leveraging the Cyber Kill Chain for Practical Hacking and its Detection via Network Forensics : Alleyne, Nik: Amazon.es: Libros

Abdulrahman Almuqbil on Twitter: "Position of attacks in the cyber kill chain 👹 #cybersecurity #hack #inforsec https://t.co/YPDpENQQOs" / Twitter
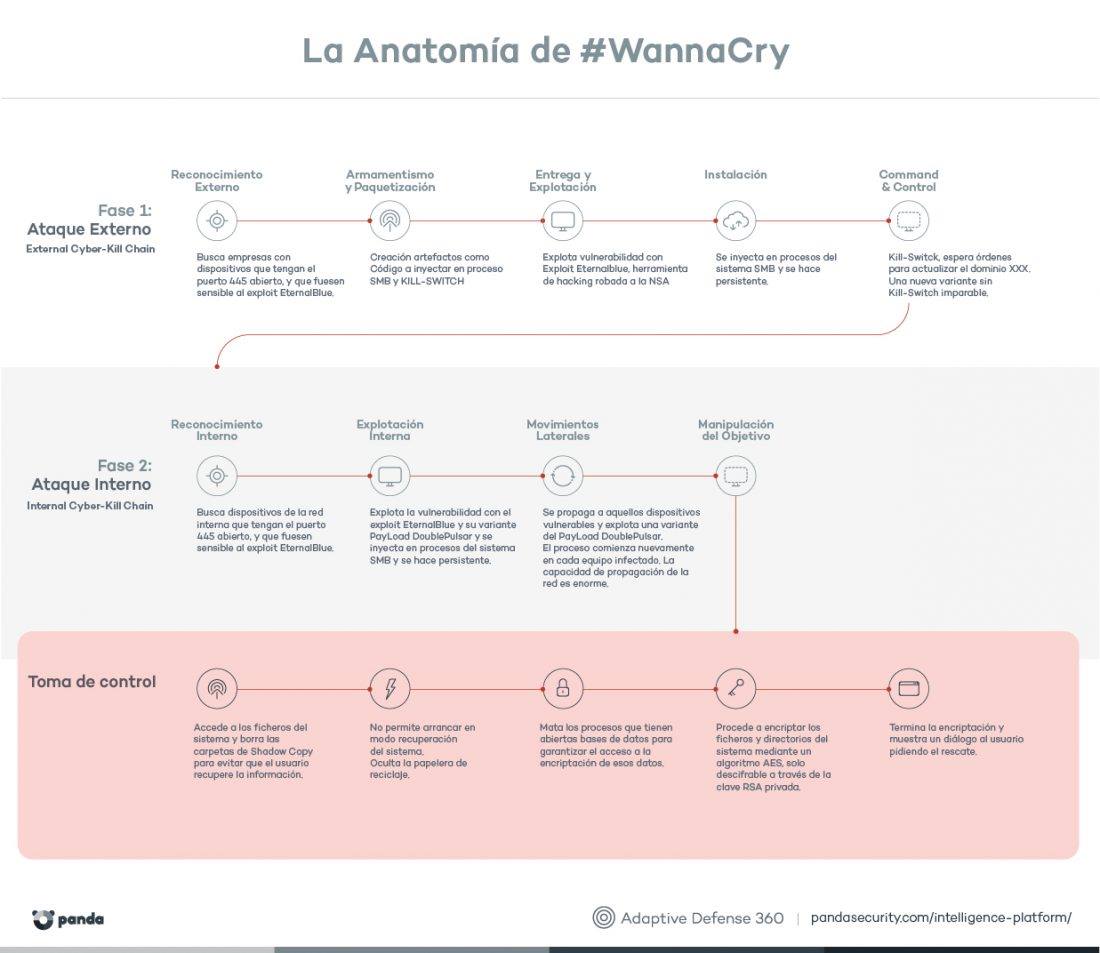
Conocimientos generales: La anatomía de WannaCry, infografía detallando el “cyber kill chain” – Seguridad de la información
![Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram](https://www.researchgate.net/publication/335024682/figure/fig1/AS:789313017098241@1565198296990/Lockheed-Martin-Cyber-Kill-Chain-CKC-22-seven-steps-The-part-that-is-specified-with.png)