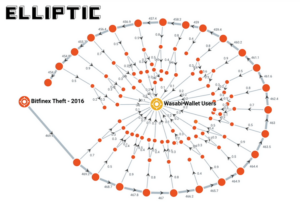
![PlusToken Scammers Didn't Just Steal $2+ Billion Worth of Cryptocurrency. They May Also Be Driving Down the Price of Bitcoin. [UPDATED 3/12/2020] - Chainalysis PlusToken Scammers Didn't Just Steal $2+ Billion Worth of Cryptocurrency. They May Also Be Driving Down the Price of Bitcoin. [UPDATED 3/12/2020] - Chainalysis](https://blog.chainalysis.com/wp-content/uploads/2022/01/5dee8bb856c1693740151751_HUkMMJNnlvZrKe9huJEhmUNUkF153JsrsLeh6G2VypJX_5rq8u4CdMYEj9lzVoWaKdqy-N3A8hjRfvA9cMUy_EAnbGk9E4g78Y4CerMowu2f_pG_70wK9KoPdpvB-lzk_fLd5HVp.png)
PlusToken Scammers Didn't Just Steal $2+ Billion Worth of Cryptocurrency. They May Also Be Driving Down the Price of Bitcoin. [UPDATED 3/12/2020] - Chainalysis

JD Supra: Two Chinese Nationals Charged with Money Laundering Over $100 Million in Cryptocurrency for North Korea
Peel Senior Link | Charlene Hendry presents at the Blockchain in Healthcare Canada Conference - Peel Senior Link

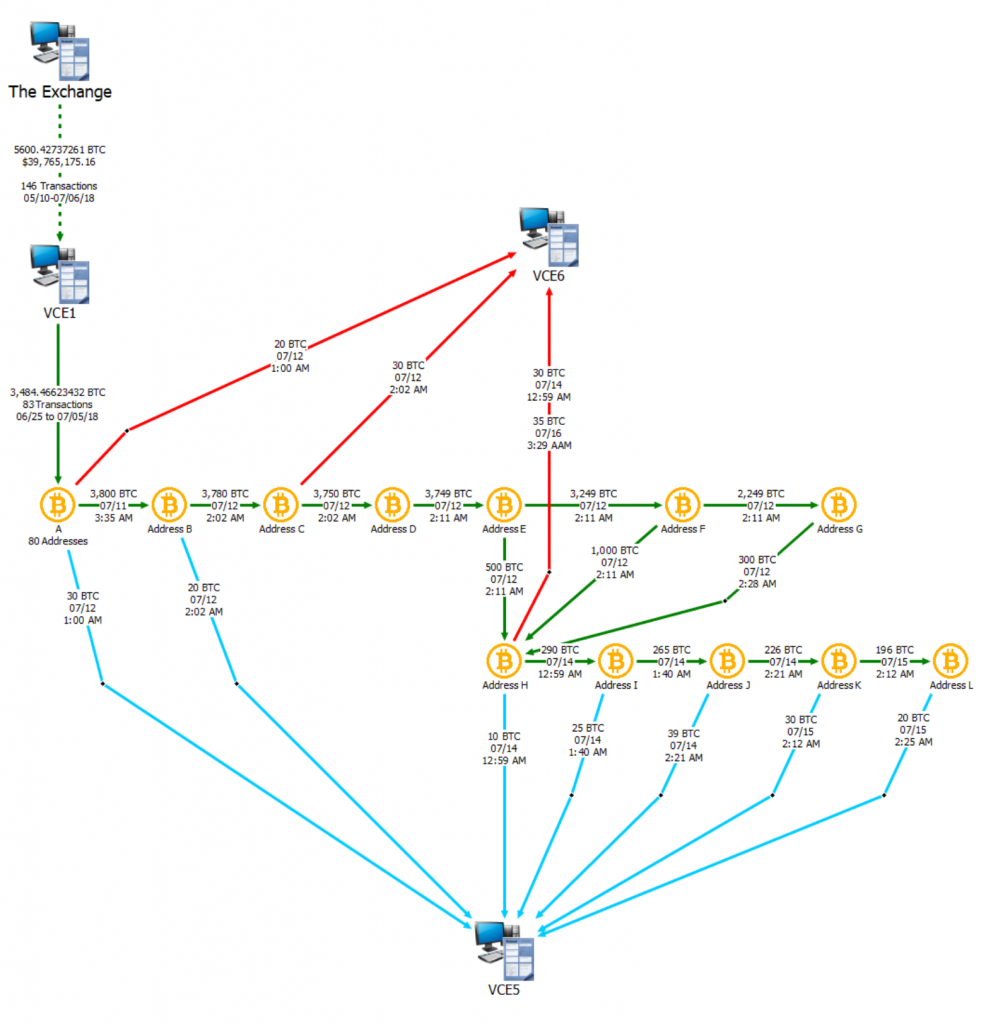
Analysis: How Chinese Nationals Linked to North Korea Laundered Hundreds of Millions of Dollars' Worth of Stolen Cryptocurrency Through Several Banks and Cryptocurrency Exchanges - CipherTrace

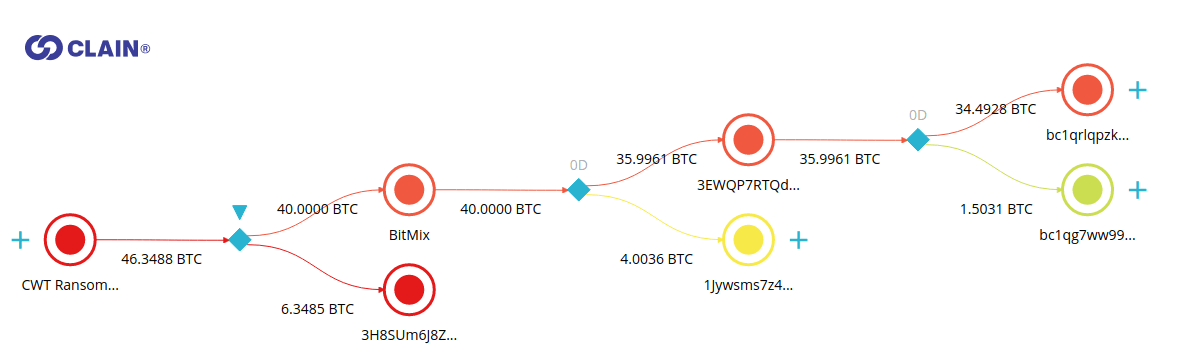
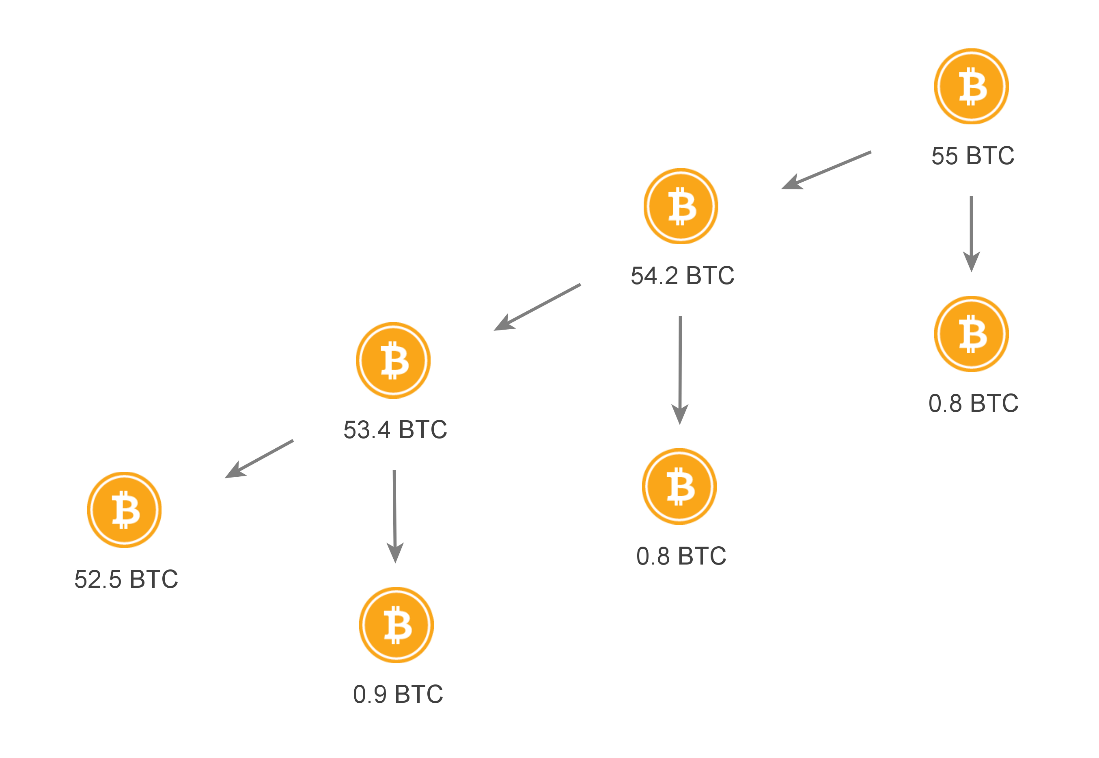
SlowMist Explains How Peel Chains Are Used To Launder Large Amounts Of Cryptocurrency | Crowdfund Insider