Inspiring trust. Church communications & organizational vulnerability : Pujol Soler, Jordi, Narbona, Juan, Díaz, José María: Amazon.es: Libros

Women Organizational Vulnerability - 𝗩𝘂𝗹𝗻𝗲𝗿𝗮𝗯𝗶𝗹𝗶𝗱𝗮𝗱, 𝗺𝘂𝗷𝗲𝗿𝗲𝘀, 𝘁𝘂𝗿𝗶𝘀𝗺𝗼 𝘆 𝗽𝗮𝗻𝗱𝗲𝗺𝗶𝗮. ¿Cómo ha impactado la pandemia por Covid-19 en las mujeres que trabajan en el turismo? | Facebook

Discussion: Organizational Needs and Issues | New Directions in Climate Change Vulnerability, Impacts, and Adaptation Assessment: Summary of a Workshop |The National Academies Press

Disaster, Hazard, Types of Hazard (Natural and Man Made Hazards), and Vulnerability (Categories of Vulnerability)

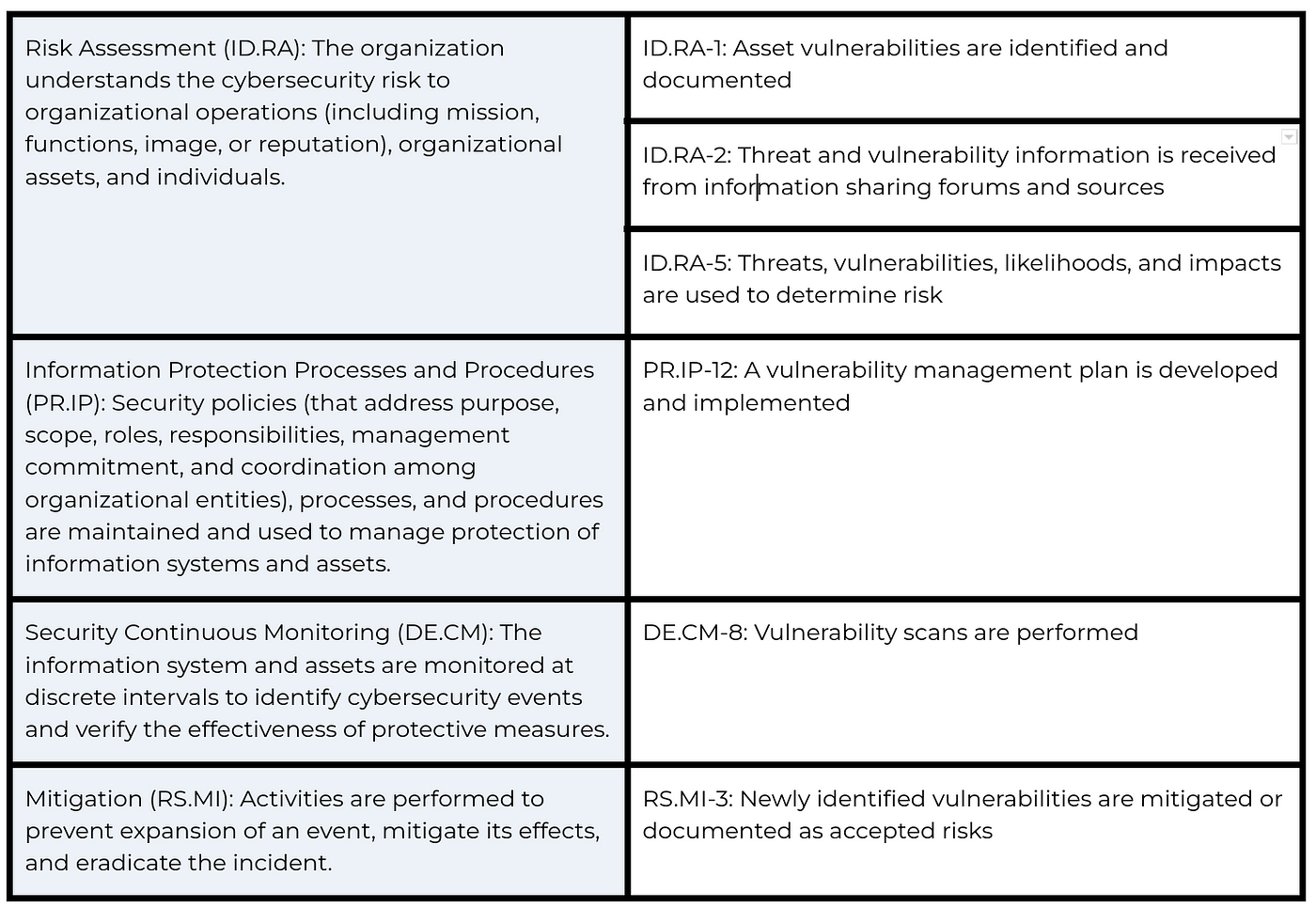
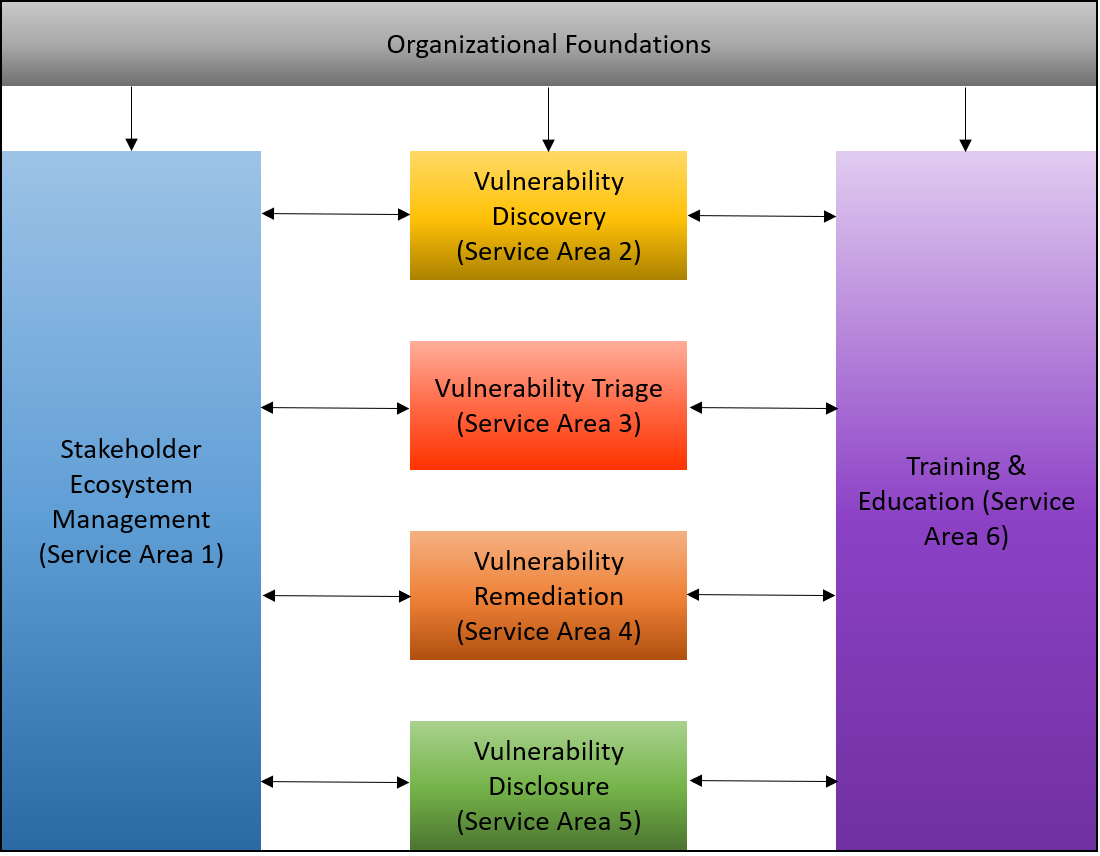
Bulwark - An Organizational Asset And Vulnerability Management Tool, With Jira Integration, Designed For Generating Application Security Reports

Organizational vulnerabilities, their consequences on hospital service... | Download Scientific Diagram

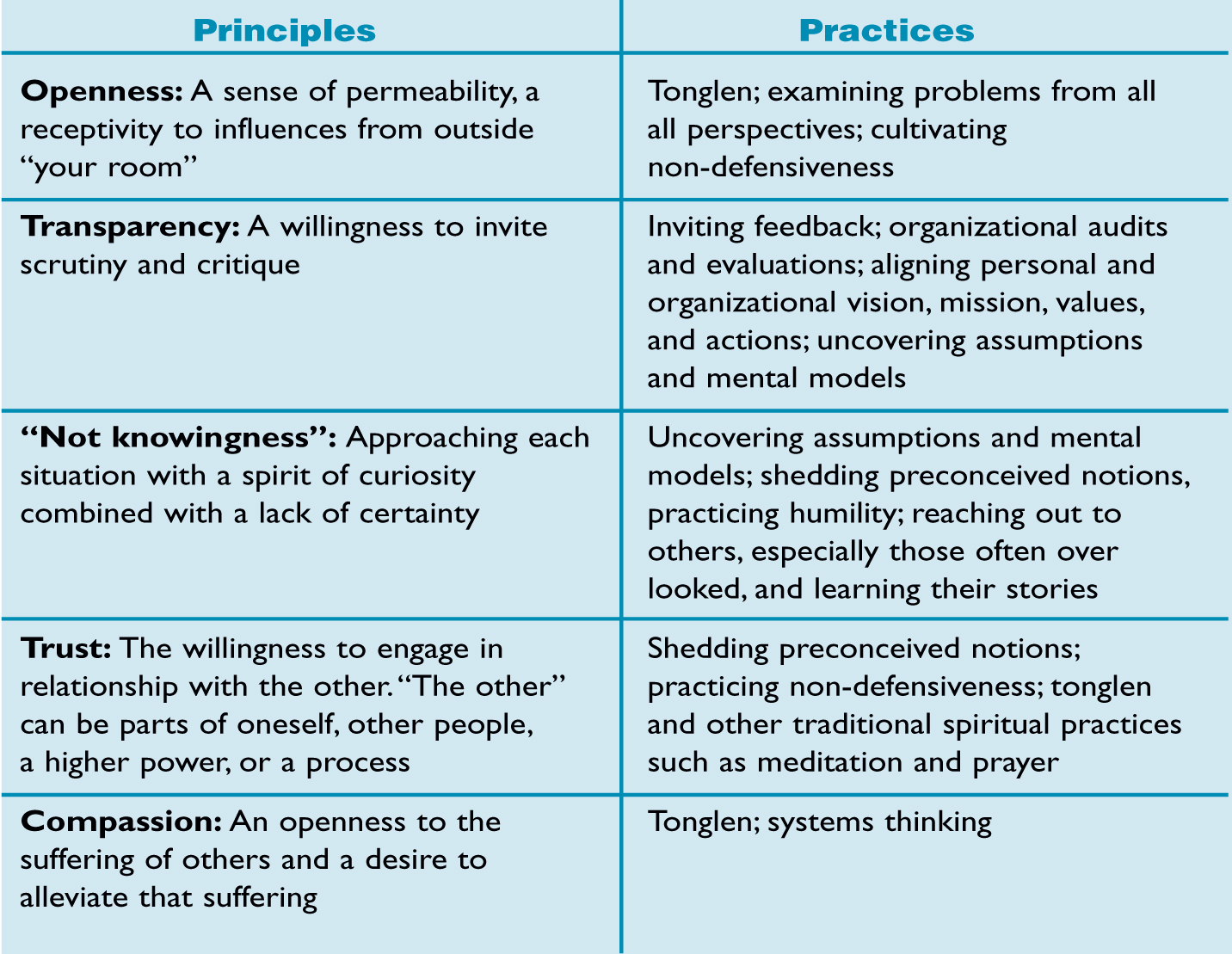
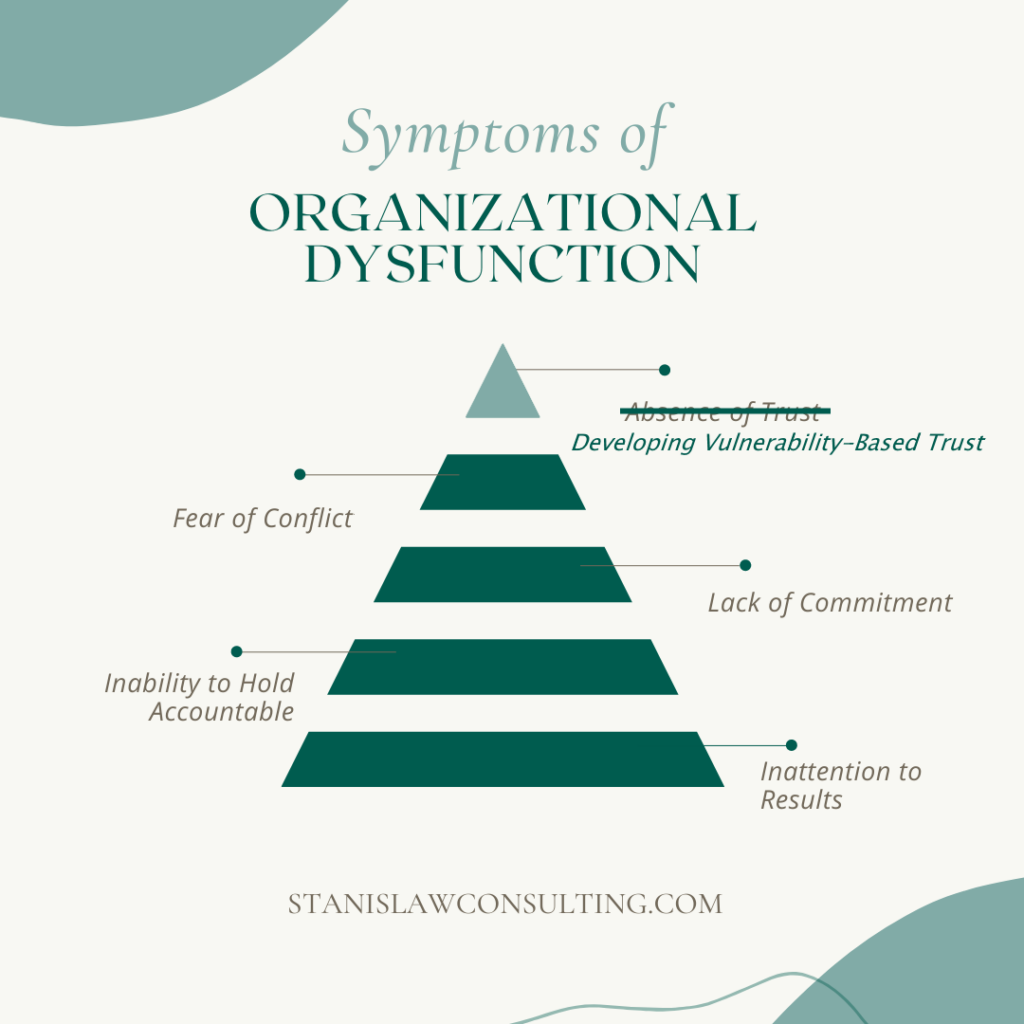
The Role of Vulnerability in Leadership: A study to understand how vulnerability contributes to personal, professional, and organizational success
Organizational Perceptions of Women's Vulnerability to Violence in the Wake of Disaster - UNT Digital Library