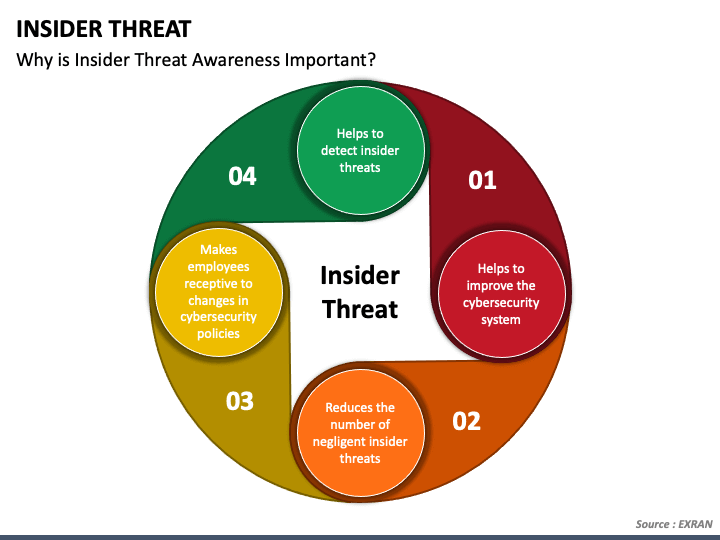
Most Companies Don't See Strategic Threats Coming Until It Is Too Late - Part 3 | Vistage Research Center
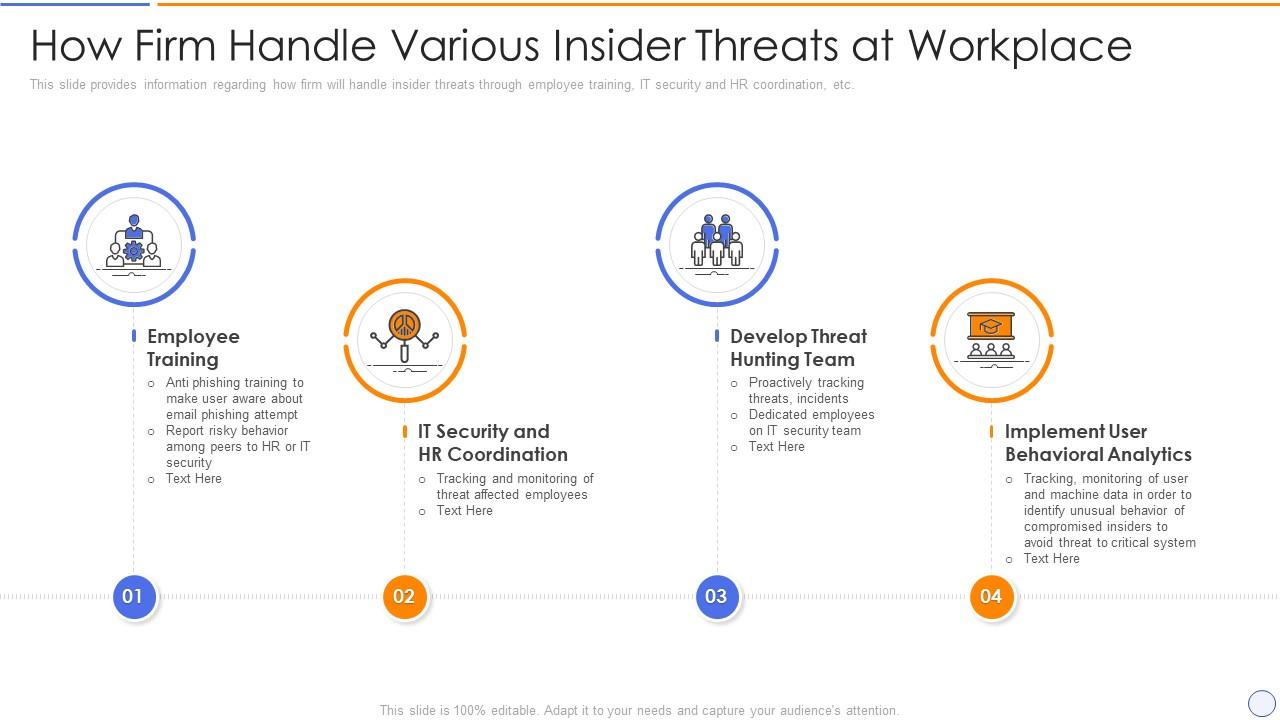
Building Organizational Security Strategy Plan How Firm Handle Various Insider Threats At Workplace | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Terrorist Use of Cryptocurrencies: Technical and Organizational Barriers and Future Threats (English Edition) eBook : Dion-Schwarz, Cynthia, Manheim, David, Johnston, Patrick B.: Amazon.es: Tienda Kindle
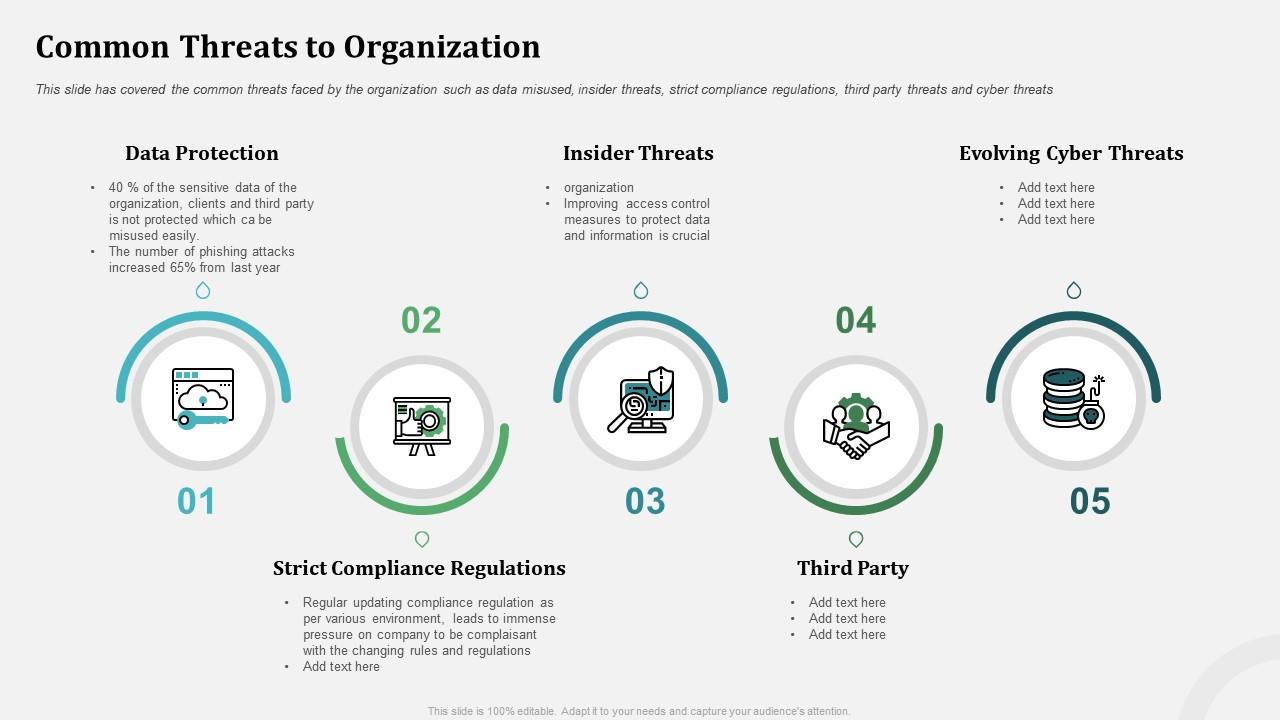
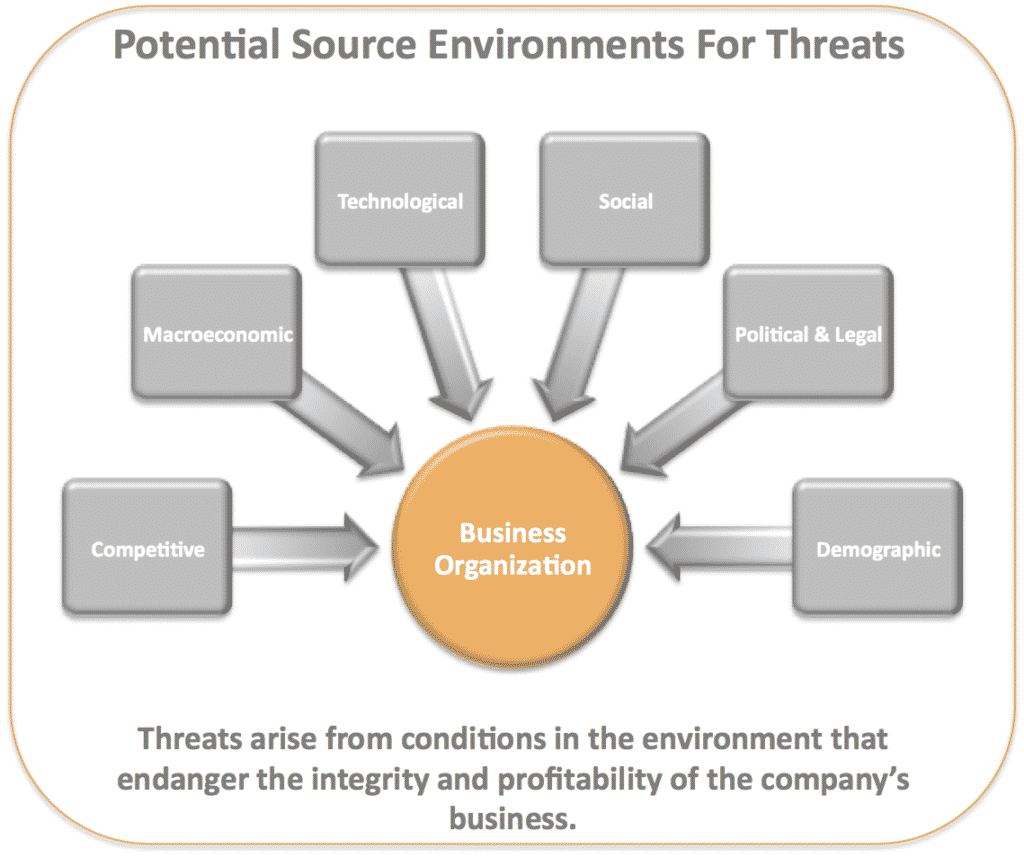
Common Threats To Organization Organizational Behavior And Employee Relationship Management | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

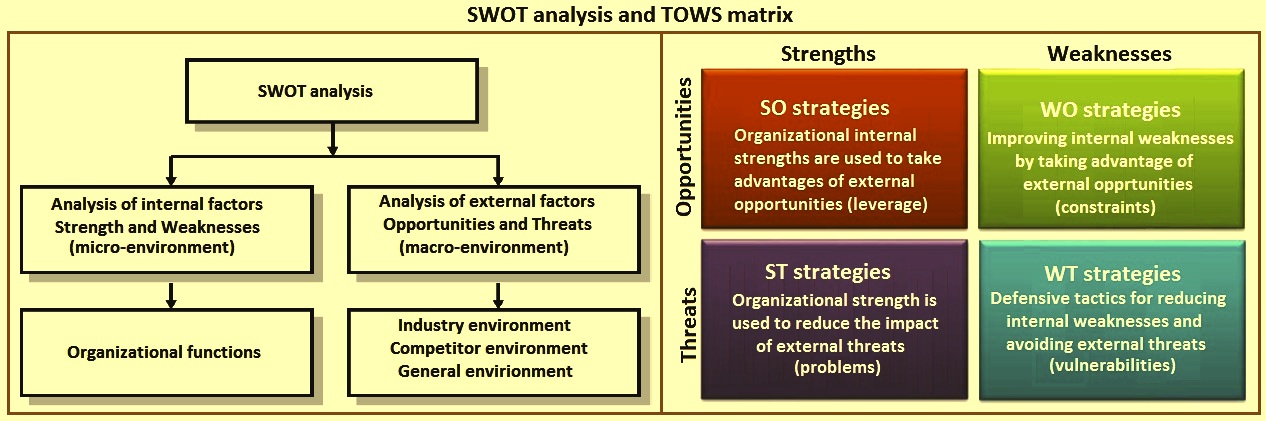
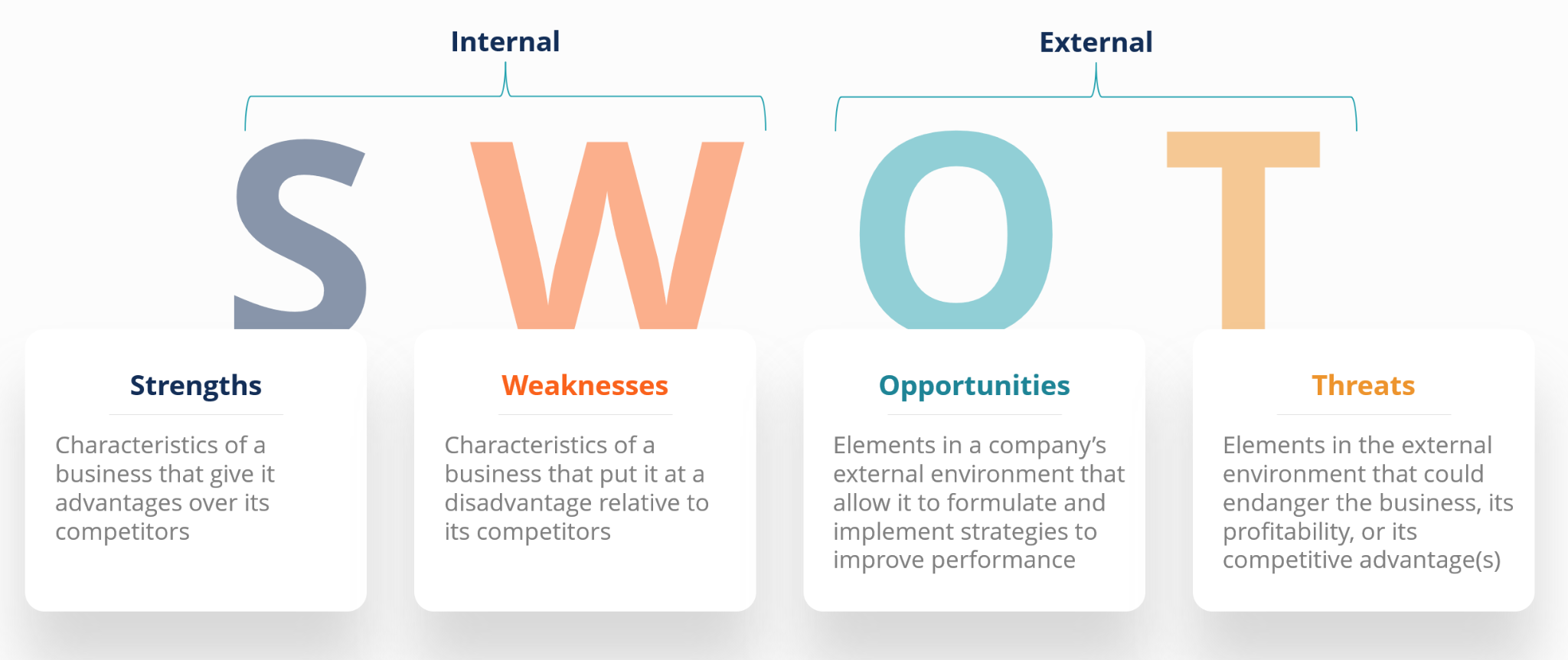
SWOT Analysis Threats Develop Organizational Productivity By Enhancing Business Process Background PDF - PowerPoint Templates
![PDF] Responding to Organizational Identity Threats: Exploring the Role of Organizational Culture | Semantic Scholar PDF] Responding to Organizational Identity Threats: Exploring the Role of Organizational Culture | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/51721e7430c06b1720087bb64cd1b176bee9c65d/22-Table4-1.png)
PDF] Responding to Organizational Identity Threats: Exploring the Role of Organizational Culture | Semantic Scholar

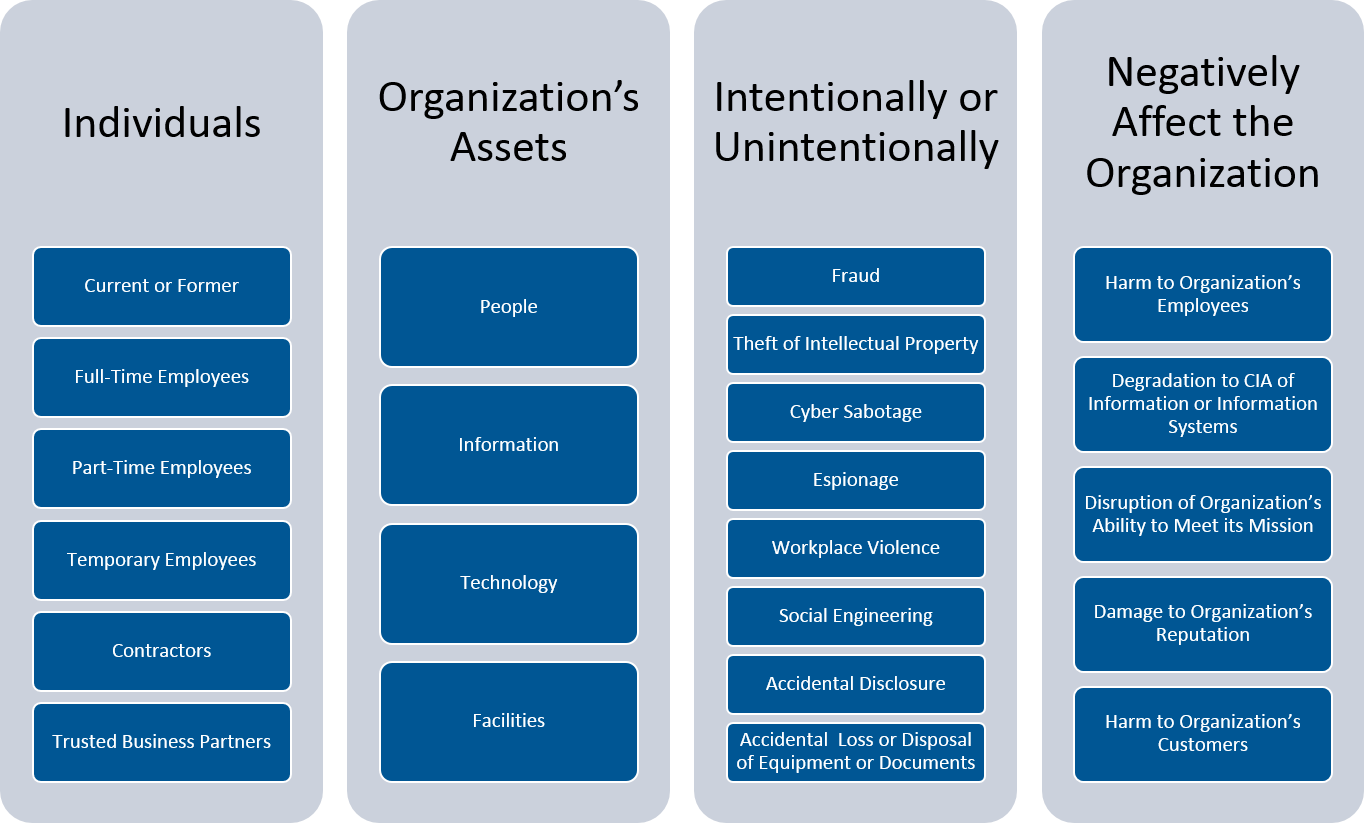
Example Insider Threat Program Organizational Structure and Data Providers | Download Scientific Diagram









:max_bytes(150000):strip_icc()/SWOTAnalysis_final-d57d99fb6e1a45bf81e84763736d87f0.png)