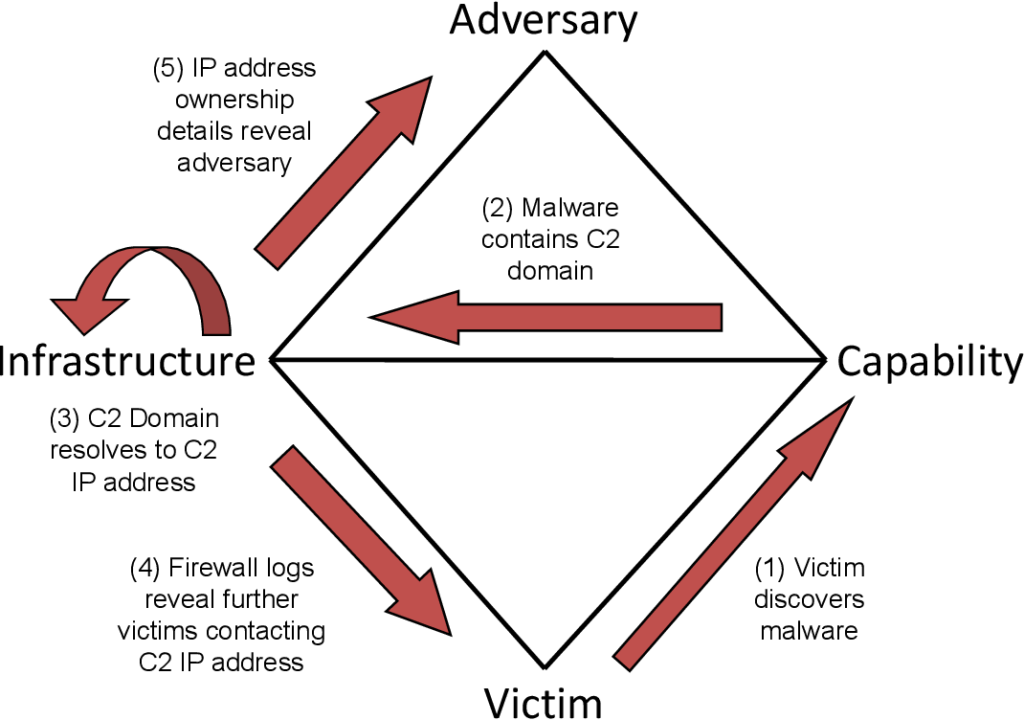
Diamond Presentation v2 0: Diamond Model for Intrusion Analysis – Applied to Star Wars' Battles - YouTube
CyCraft Classroom: MITRE ATT&CK vs. Cyber Kill Chain vs. Diamond Model | by CyCraft Technology Corp | CyCraft | Medium
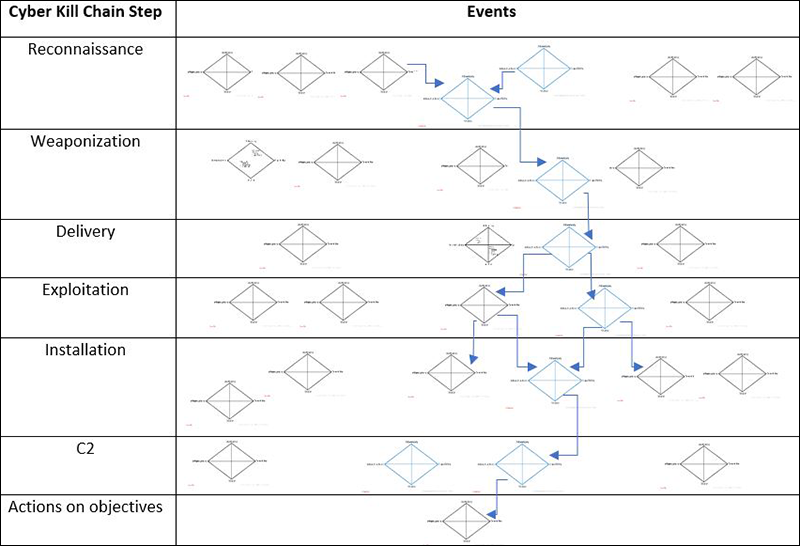
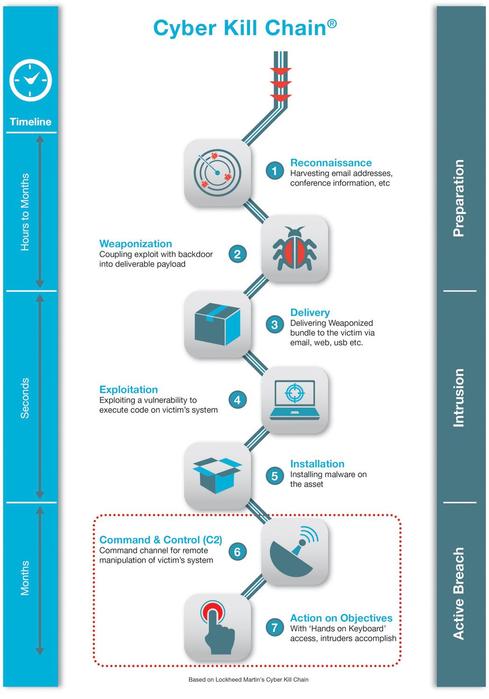
CyCraft Classroom: MITRE ATT&CK vs. Cyber Kill Chain vs. Diamond Model | by CyCraft Technology Corp | CyCraft | Medium
CyCraft Classroom: MITRE ATT&CK vs. Cyber Kill Chain vs. Diamond Model | by CyCraft Technology Corp | CyCraft | Medium

John Lambert on Twitter: "Getting started in intrusion analysis? Here are 3 seminal papers: 1⃣Cyber Kill Chain by @killchain, @mikecloppert, & @rohanamin: https://t.co/stAnlIKv7v 2⃣Diamond Model by @cnoanalysis et al: https://t.co/3gK6Ecy7e6 ...

An evaluation of potential attack surfaces based on attack tree modelling and risk matrix applied to self-sovereign identity - ScienceDirect
CyCraft Classroom: MITRE ATT&CK vs. Cyber Kill Chain vs. Diamond Model | by CyCraft Technology Corp | CyCraft | Medium
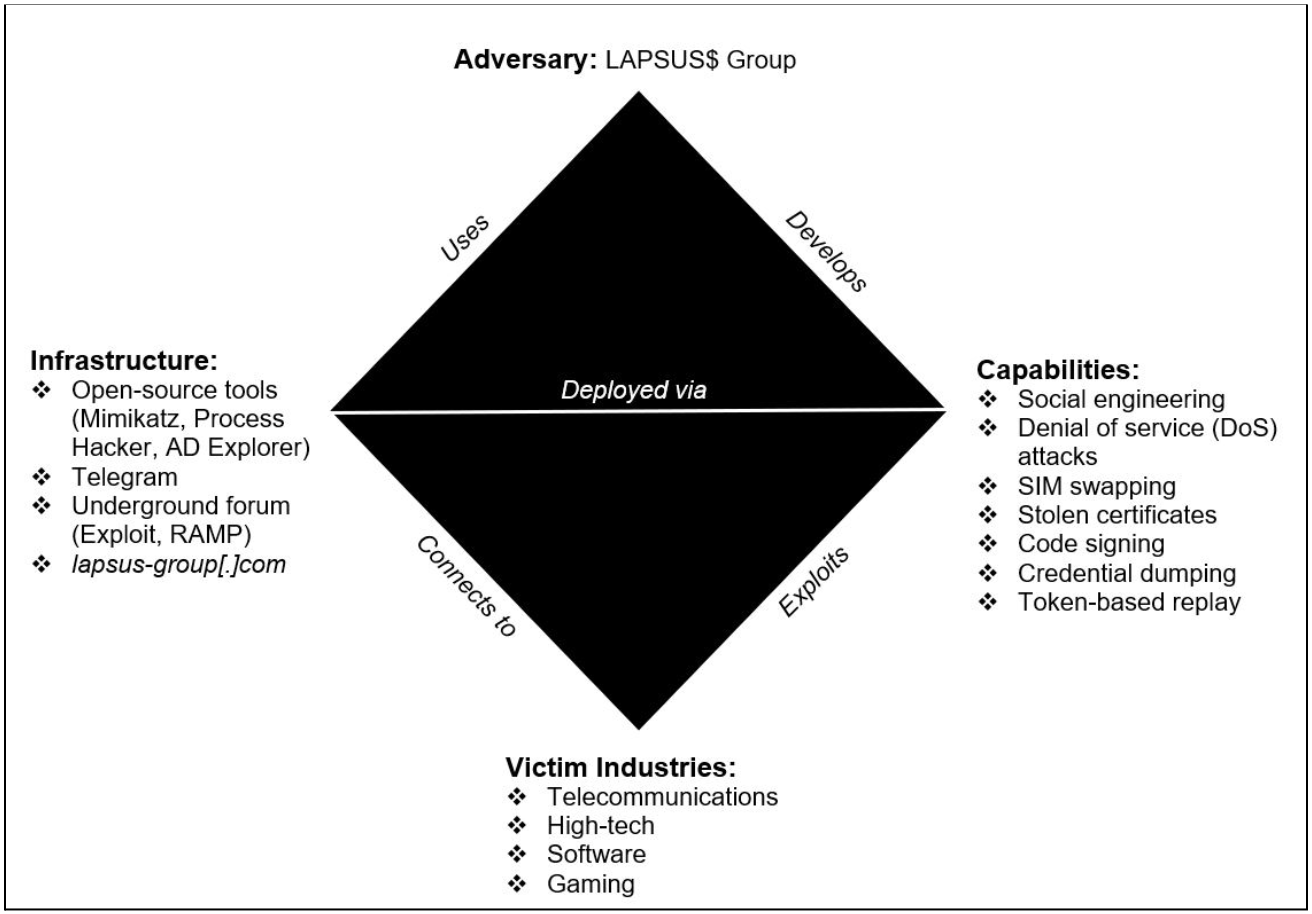
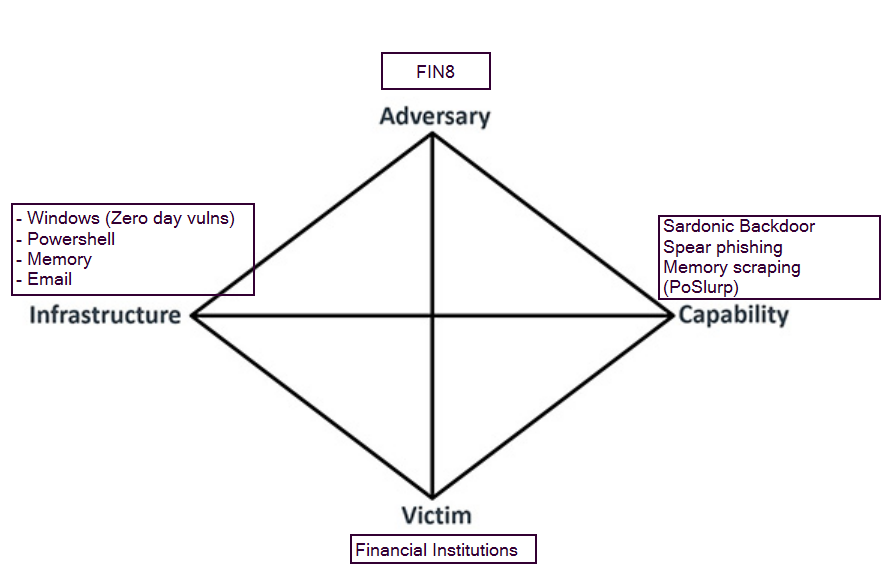
Relapse of LAPSUS$: A Cyber Threat Intelligence Case Study (Kate Esprit & Meghan Jacquot) | WiCyS - Women in Cybersecurity
![PDF] Applying the Kill Chain and Diamond Models to Microsoft Advanced Threat Analytics | Semantic Scholar PDF] Applying the Kill Chain and Diamond Models to Microsoft Advanced Threat Analytics | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ac9b12f266663e9de690e01c5904877bd786299d/3-Figure5-1.png)