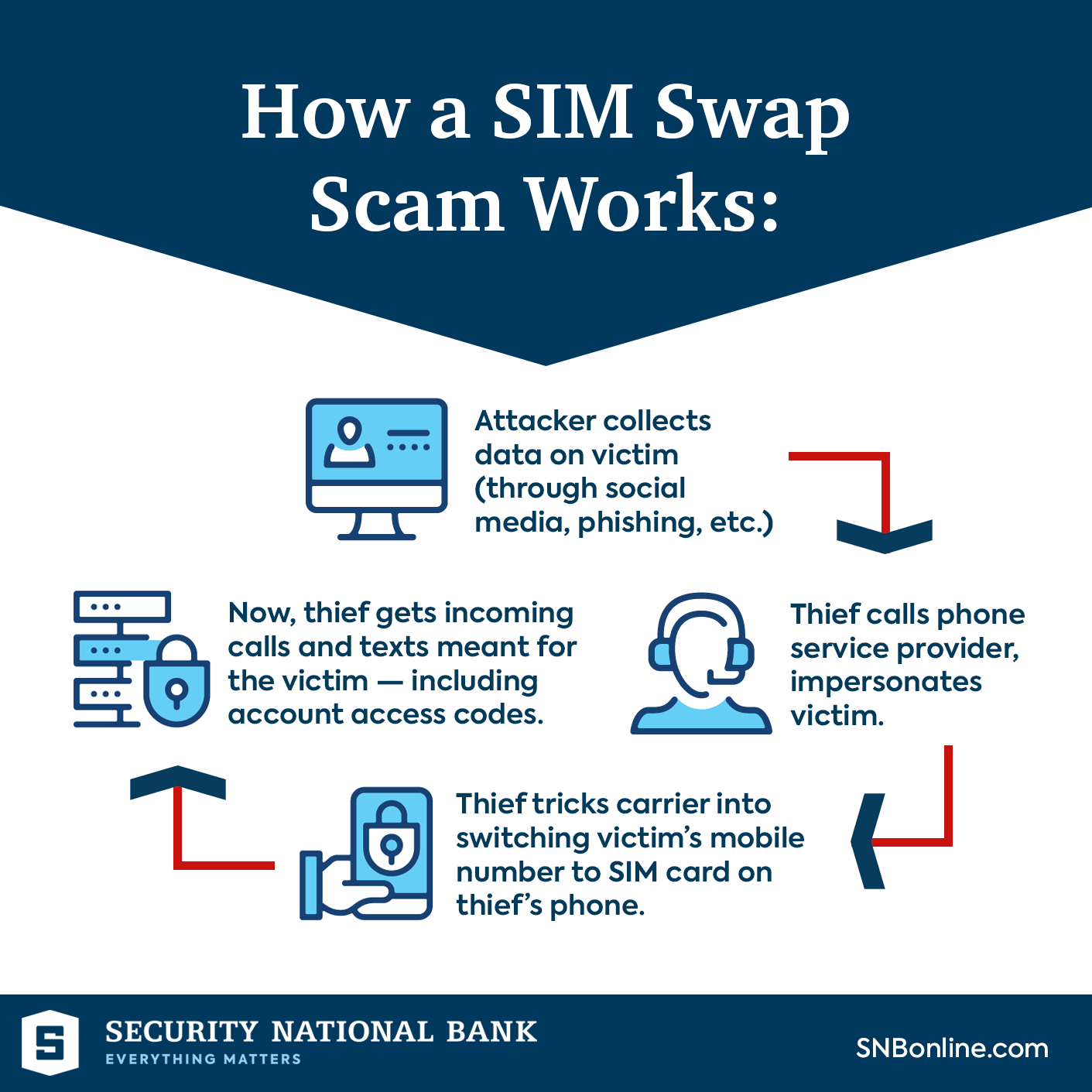
More than 110,000 Australians caught up in September's Facebook cyber-attack | Facebook | The Guardian

Spoofing attack by a scammer. A man holding his cell phone while his bank is calling. Fake spoofed number of the criminal trying to do a phishing atta Stock Photo - Alamy

Spoofing attack by a scammer. A man holding his cell phone while his bank is calling. Fake spoofed number of the criminal trying to do a phishing atta Stock Photo - Alamy